Share your love
How to Secure Nginx with Let’s Encrypt on AlmaLinux 8

In this article, we want to teach you How to Secure Nginx with Let’s Encrypt on AlmaLinux 8.
Let’s Encrypt is a free, automated, and open certificate authority run by the nonprofit Internet Security Research Group (ISRG).
In this article, you will set up a TLS/SSL certificate from Let’s Encrypt on an AlmaLinux 8 server running Nginx as a web server.
Steps To Secure Nginx with Let’s Encrypt on AlmaLinux 8
To complete this article you need some requirements first.
Requirements
Log in as a non-root user with sudo privileges and set up a basic firewall. you can check the Initial server setup article for AlmaLinux 8.
You need to install Nginx on AlmaLinux 8 and set up Nginx server blocks. To do this you can visit our article about How To Install Nginx on AlmaLinux 8.
Also, you need a fully registered domain name.
When you are completely done with these requirements you can start to secure your Nginx with Let’s Encrypt on AlmaLinux 8.
Install Certbot Let’s Encrypt Client on ALmaLinux 8
By default, the certbot package is not available in the DNF package manager. you need to enable the EPEL repository.
Run the following command to add the EPEL repository on AlmaLinux 8:
sudo dnf install epel-release
Now you can install all of the certbot packages with the following command:
sudo dnf install certbot python3-certbot-nginx
At this point, you have installed the Let’s Encrypt client. To get the certificates you need to update your firewall settings first.
Update Firewall Settings on AlmaLinux
To check which services are already enabled run the following command:
sudo firewall-cmd --permanent --list-all
In your output you will see:
Output public target: default icmp-block-inversion: no interfaces: sources: services: cockpit dhcpv6-client http https ssh ports: protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules:
Note: If you don’t see HTTP and HTTPS in your services list run the following commands to enable them:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
To apply these changes reload the firewall with the following command:
sudo firewall-cmd --reload
Now you are ready to get your SSL certificate.
Get an SSL certificate with Let’s Encrypt on AlmaLinux 8
Here you can request an SSL certificate for your domain.
Note: If you want to install a single certificate that is valid for multiple domains or subdomains, you can pass them as additional parameters to the command.
Here our domain name is nginx.orcacore.net you should replace it with your own domain in the commands.
sudo certbot --nginx -d nginx.orcacore.net -d www.nginx.orcacore.net
For the single domain you can use:
sudo certbot --nginx -d nginx.orcacore.netYou will be asked to enter your email address and then agree to the terms of services.
Now call certbot without any domains for domain information during the certificate request procedure:
sudo certbot --nginx
You will be asked to select your domain name you can leave it blank to choose both or if you use a single domain choose one of them.
Then select Renew & replace the certificate.
In your output you will see:
Output
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/nginx.orcacore.net/fullchain.pem
Key is saved at: /etc/letsencrypt/live/nginx.orcacore.net/privkey.pem
This certificate expires on 2021-12-25.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
Deploying certificate
Successfully deployed certificate for nginx.orcacore.net to /etc/nginx/conf.d/nginx.orcacore.net.conf
Successfully deployed certificate for www.nginx.orcacore.net to /etc/nginx/conf.d/nginx.orcacore.net.conf
Your existing certificate has been successfully renewed, and the new certificate has been installed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -At this point, when you are finished using certbot, you can check your SSL certificate status. Type the following link to your web browser:
Remember to replace the domain name.
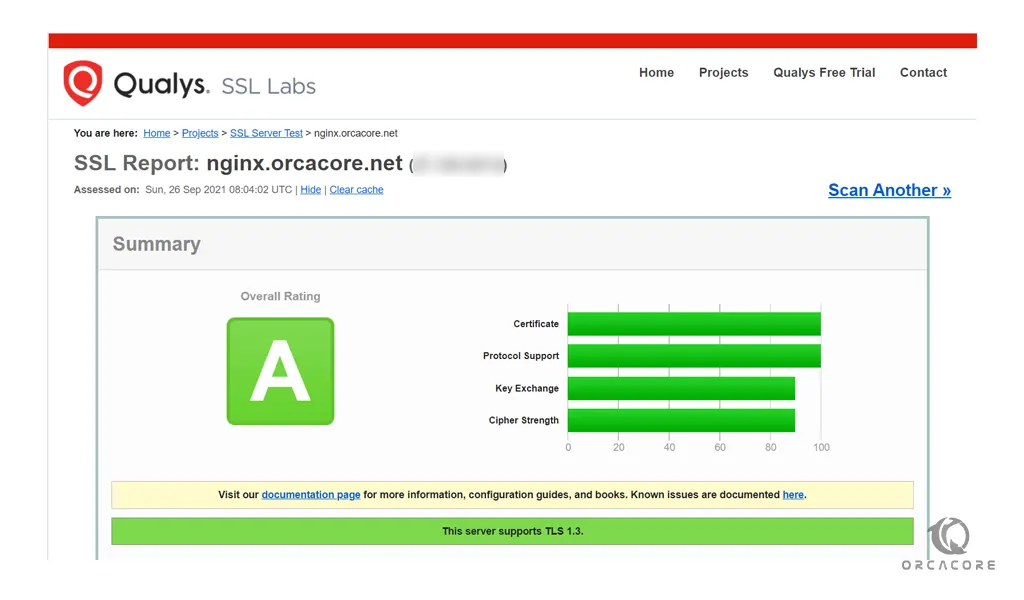
https://www.ssllabs.com/ssltest/analyze.html?d=nginx.orcacore.netHere you will get an A grade from your SSL certificate. Also, you can access your website using the HTTPs prefix.
Now you should renew certificates periodically to keep this setup working.
Let’s see how to do that.
Set up Auto-renewal for SSL certificates on AlmaLinux 8
Let’s Encrypt certificates are valid for 90 days, but it’s recommended that you renew the certificates every 60 days.
certbot auto-renew Nginx
You can test automatic renewal for your certificates with the following command:
sudo certbot renew --dry-run
your output should similar to this:
Output
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/nginx.orcacore.net.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Account registered.
Simulating renewal of an existing certificate for nginx.orcacore.net and www.nginx.orcacore.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations, all simulated renewals succeeded:
/etc/letsencrypt/live/nginx.orcacore.net/fullchain.pem (success)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Also, it is safe to create a cron job that runs every week, or even every day.
To edit the crontab for the root user run the following command:
sudo crontab -e
Then, add the following line to the empty file:
0 0,12 * * * python -c 'import random; import time; time.sleep(random.random() * 3600)' && certbot renew --quiet
When you are done, save and close the file with the “:wq”.
Conclusion
At this point, you learn to install the Let’s Encrypt client Certbot, download SSL certificates for your domain, and set up automatic certificate renewal.
Hope you enjoy this article about How to Secure Nginx with Let’s Encrypt on AlmaLinux 8.
You may be like these articles:
Secure Nginx with Let’s Encrypt on AlmaLinux 9