Share your love
Set Up Password Authentication with Apache on Debian 11

In this tutorial, we want to teach you How To Set Up Password Authentication with Apache on Debian 11.
Password-based authentication is the process of gaining access to resources to which one is entitled with the help of a set of credentials containing a username and password. This is a rampantly used method known for process simplicity and low cost.
When a password is created, a copy of that is stored by the website or system in a secure credentials database against which the server would compare further login attempts. In order to avoid a field day for the hackers, it’s imperative that password-based authentication is enabled in encrypted form in a password vault.
Set Up Password Authentication with Apache on Debian 11
To set up Apache password authentication, you need some requirements.
Requirements
You must log in to your server as a non-root user with sudo privileges. To do this, you can follow this guide on Initial Server Setup with Debian 11.
Also, you need to have Apache installed on your server. You can visit the installation part of How To Install Apache on Debian 11.
Now follow the steps below to complete this guide.
Install the Apache Utilities Package on Debian 11
In order to create the file that will store the passwords needed to access our restricted content, we will use a utility called htpasswd. This is found in the apache2-utils package within the Debian repositories.
First, update your local package index with the following command:
sudo apt update
Then, use the command below to install the Apache utility package:
sudo apt install apache2-utils
Create a Password File with Apache Utilities on Debian 11
At this point, you can access to the htpasswd command. We can use this to create a password file that Apache can use to authenticate users. We will create a hidden file for this purpose called .htpasswd within our /etc/apache2 configuration directory.
Use the following command to create your user, here we named it olivia:
sudo htpasswd -c /etc/apache2/.htpasswd olivia
You will be asked to enter a password:
Output New password: Re-type new password: Adding password for user olivia
If you want to add more users, run the above command without the -c option:
sudo htpasswd /etc/apache2/.htpasswd another_user
List your username and the encrypted password for each record with the command below:
cat /etc/apache2/.htpasswd
Output
olivia:$apr1$KBkzRjED$YuwKrvI7nrpUgZDRNTyJs0
Configure Apache Password Authentication on Debian 11
At this point, you have a file with your users and passwords in a format that Apache can read on Debian 11.
Now you must configure Apache to check this file before serving your protected content. To do this, you have two options to choose from:
- Edit the Apache configuration and add our password protection to the virtual host file. This will generally give better performance because it avoids the expense of reading distributed configuration files. If you have this option, this method is recommended.
- If you do not have the ability to modify the virtual host file (or if you are already using
.htaccess files for other purposes), you can restrict access using an.htaccessfile. Apache uses.htaccess files in order to allow certain configuration items to be set within a file in a content directory. The disadvantage is that Apache has to re-read these files on every request that involves the directory, which can impact performance.
We will show you both ways and choose the one that is best for you.
Configure Access Control within the Virtual Host Definition
In this step, we will use the 000-default.conf file that holds the default virtual host installed through Debian’s Apache package. Open the file with your favorite text editor, we use vi:
sudo vi /etc/apache2/sites-enabled/000-default.conf
Inside, with the comments stripped, the file should look similar to this:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>To set up authentication, you will need to target the directory you wish to restrict with a <Directory ___> block. In our example, we’ll restrict the entire document root, but you can modify this listing to only target a specific directory within the web space.
Within this directory block, specify that we wish to set up Basic authentication. For the AuthName, choose a realm name that will be displayed to the user when prompting for credentials. Use the AuthUserFile directive to point Apache to the password file we created. Finally, we will require a valid-user to access this resource, which means anyone who can verify their identity with a password will be allowed in:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
<Directory "/var/www/html">
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
</Directory>
</VirtualHost>When you are done, save and close the file.
Restart Apache to apply the changes:
sudo systemctl restart apache2
The directory you specified should now be password-protected.
Configure Access Control with .htaccess Files
If you want to set up password protection using .htaccess files instead, you should begin by editing the main Apache configuration file to allow .htaccess files:
sudo vi /etc/apache2/apache2.conf
Find the <Directory> block for the /var/www directory that holds the document root. Turn on .htaccess processing by changing the AllowOverride directive within that block from “None” to “All”:
. . .
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
. . .When you are done, save and close the file.
Next, we need to add a .htaccess file to the directory we wish to restrict. We’ll restrict the entire document root (the entire website) which is based at /var/www/html, but you can place this file in any directory you wish to restrict access to:
sudo vi /var/www/html/.htaccess
Within this file, specify that we wish to set up Basic authentication. For the AuthName, choose a realm name that will be displayed to the user when prompting for credentials. Use the AuthUserFile directive to point Apache to the password file we created. Finally, we will require a valid-user to access this resource, which means anyone who can verify their identity with a password will be allowed in:
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-userWhen you are done, save and close the file.
Restart Apache to apply the changes:
sudo systemctl restart apache2
To confirm that your content is protected, try to access your restricted content in a web browser:
http://your-server-ip
You should be presented with a username and password prompt:
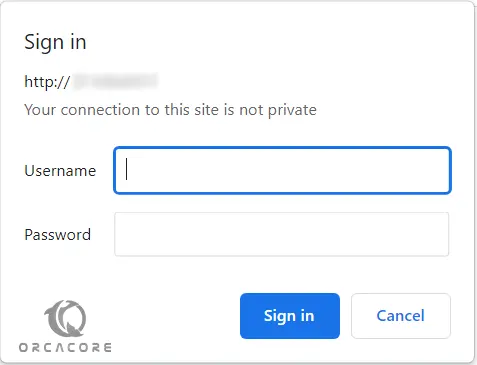
If you enter the correct credentials, you will be allowed to access the content.
Conclusion
At this point, you learn to Set up Password Authentication With Apache on Debian 11. However, passwords are also one of the most insecure forms of user authentication out there. It is recommended to use TLS encryption. You can visit our guide on Secure Apache with Let’s Encrypt on Debian 11.
Hope you enjoy it.



