Share your love
AppArmor Configuration on Debian 12 Bookworm

This guide intends to teach you AppArmor Configuration on Debian 12 Bookworm. AppArmor which stands for Application Armor is a security module for Linux Kernel. It helps you to protect your operating system and applications from external or internal threats by enforcing security policies, which are known as profiles.
- AppArmor Usage in Debian
- Step-by-Step Guide For AppArmor Configuration on Debian 12 Bookworm
- Step 1 - Enable AppArmor on Debian 12
- Step 2 - Check the Current AppArmor Profile on Debian 12
- Step 3 - Modify AppArmor Profiles on Debian 12
- Step 4 - Create a New AppArmor Profile on Debian 12
- Step 5 - Disable and Remove AppArmor
- Summing Up AppArmor Configuration in Debian
AppArmor Usage in Debian
AppArmor uses a Mantadory Access Control (MAC) system to restrict the capabilities of programs. Each of these programs can have a profile that allows what files it can access and what operations it can perform.
Also, AppArmor profiles have two modes which are:
Enforcement Mode: Actively restricting actions
Complain Mode: Logging violations without enforcing
AppArmor helps to increase the Debian system security with an additional protection layer. Debian ships with AppArmor profiles for several common applications, and users can create or modify profiles for other applications as needed.
Also, AppArmor is a flexible and easy-to-use security module rather than SELinux.
Step-by-Step Guide For AppArmor Configuration on Debian 12 Bookworm
As you may know, AppArmor is installed by default in Debian 12. You can log in to your server as a root or non-root user with sudo privileges. Then, proceed to the following steps to start your AppArmor configuration.
Step 1 – Enable AppArmor on Debian 12
As we said, AppArmor is already installed on the Debian server. Also, it must be enabled on Debian 12. You can verify it by using the command below:
cat /sys/module/apparmor/parameters/enabledIt will show you Y as Yes, which means your AppArmor is enabled. If it isn’t enabled, you can follow the steps below.
AppArmor must be enabled from the Linux kernel command line in the bootloader. To do this, create the desired directory and use the following commands:
# sudo mkdir -p /etc/default/grub.d
# echo 'GRUB_CMDLINE_LINUX_DEFAULT="$GRUB_CMDLINE_LINUX_DEFAULT apparmor=1 security=apparmor"' \
| sudo tee /etc/default/grub.d/apparmor.cfg
# sudo update-grub
# sudo rebootStep 2 – Check the Current AppArmor Profile on Debian 12
At this point, you can check the current profile that is loaded for each app and process. To do this, you can run the following command:
sudo aa-statusExample Output:
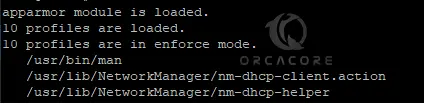
As you can see in the above example, 10 profiles are loaded and they are in enforce mode.
Step 3 – Modify AppArmor Profiles on Debian 12
At this point, you can modify your profiles, you can change the modes to complain and enforce mode. To set a profile to complain mode, you can use the command below:
sudo aa-complain your-profileFor example:
sudo aa-complain /usr/bin/manOutput
Setting /usr/bin/man to complain mode.Note: If you get the aa-complain command not found error, you must install the AppArmor Utils:
sudo apt install apparmor-utils
To set a profile to enforce mode, you can run the command below:
sudo aa-enforce your-profileFor example:
sudo aa-enforce /usr/bin/manOutput
Setting /usr/bin/man to enforce mode.
If you plan to modify changes to all your profiles on Debian 12, you can use the following command:
# sudo aa-complain /etc/apparmor.d/*
And
# sudo aa-enforce /etc/apparmor.d/*Step 4 – Create a New AppArmor Profile on Debian 12
At this point, you can create a new profile on Debian 12. But first, you must find the applications that require security and they haven’t any profile in AppArmor. To do this, you can use the command below:
sudo aa-unconfined
Output
555 /usr/sbin/sshd (sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups) not confined
As you can see in the above example, sshd needs security but is not confined to AppArmor. So, you can create a new SSHD profile on Debian 12. To do this, you can use the command below:
sudo aa-genprof sshdDuring the process, press F to finish your setup. By default, it will created as the enforce mode.
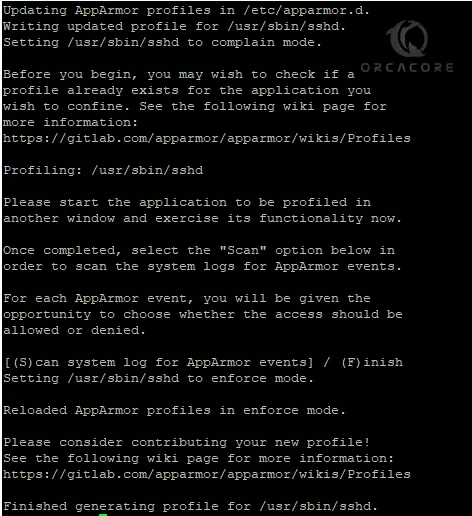
Now you must reload the AppArmor service to apply the changes. To do this, run the command below:
sudo systemctl reload apparmor.serviceNext, you can verify that your profile has been created in enforce mode with the command below:
cat /sys/kernel/security/apparmor/profilesExample Output:
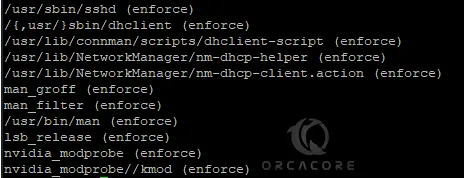
Step 5 – Disable and Remove AppArmor
If you want to disable your AppArmor service, you can stop the service and disable it by using the following commands:
# sudo systemctl stop apparmor
# sudo systemctl disable apparmor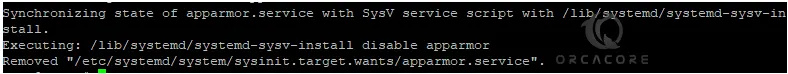
Also, you can remove the AppArmor completely from your server with the command below:
sudo apt remove --assume-yes --purge apparmor
Summing Up AppArmor Configuration in Debian
AppArmor is an essential component of Debian’s security. It provides an effective and manageable way to secure applications by defining and enforcing specific access controls. It will increase your Debian security and it is more flexible like other security options like SELinux.
At this point, you have learned AppArmor configuration including enabling, creating profiles, modifying them, and disabling AppArmor on Debian 12. Hope you enjoy it.
Also, you may like to read the following articles:
Ubuntu 22.04 ProFTPD Setup Tutorial
Nginx Proxy Manager Setup on Debian 12



