Share your love
Improve Security with TLS 1.3 on Windows Server 2022

This guide intends to teach you to Improve Security with TLS 1.3 on Windows Server 2022. TLS 1.3 stands for Transport Layer Security version 1.3. It is the most recent version of the TLS protocol, a standard protocol for securing internet connections. It is also, compared to older versions TLS 1.3 has the following improvements:
- Enhanced Security
- Improved Speed
- Forward Secrecy
Now you can follow the steps below to enable TLS 1.3.
Steps To Enable and Improve Security with TLS 1.3 on Windows Server 2022
As you may know, Windows Server 2022 supports TLS 1.3. You need to log in to your Windows Server as an admin user and follow the steps below.
Also, you need to be sure your system is up to date and doesn’t have any pending updates.
You can enable TLS 1.3 by using the following methods:
- Use Registry Editor
- Through PowerShell
Method 1 – Enable TLS 1.3 with Registry Editor on Windows Server 2022
At this point, you can press Win + R and type regedit to open the Registry Editor.
From the Registry Editor, navigate to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
Then, right-click on Protocols, create a new key, and name it TLS 1.3.
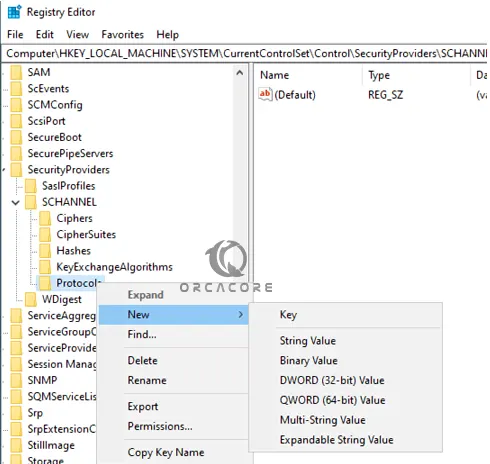
Next, inside your TLS 1.3 folder, create two new keys named Server and Client.
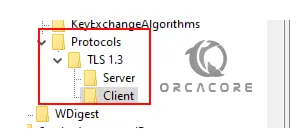
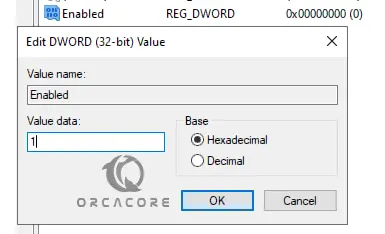
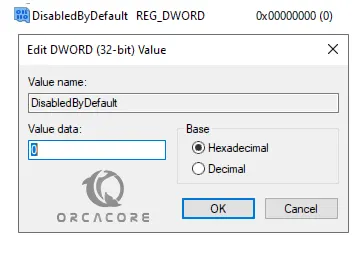
Now for each, you need to create a new DWORD (32-bit) Value named Enabled with a value of 1 and a DWORD (32-bit) Value named DisabledByDefault with a value of 0.
Method 2 – Enable TLS 1.3 via PowerShell on Windows Server 2022
If you prefer to use PowerShell commands, you can run your PowerShell as an administrator and use the following commands to enable TLS 1.3:
# New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Force
# New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Name 'Enabled' -Value '1' -PropertyType 'DWord'
# New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Name 'DisabledByDefault' -Value '0' -PropertyType 'DWord'
Note: You need to do these for the client too.
Test TLS 1.3 is Working Correctly
Once you are done, you need to restart your server to apply the changes.
To test your TLS 1.3, you can use a network protocol analyzer like Wireshark. For this purpose, you can check this guide on Installing Wireshark on Windows Server 2022.
Conclusion
It’s important to note that recent versions of Windows support TLS 1.3, allowing applications and services running on Windows to benefit from the new security enhancements. Hope you enjoy it.
Also, you may like to read the following articles:
Delete Unnecessary Files on Windows 11



